(Continued from 1st post)
![[Image: jpg]](https://d2skuhm0vrry40.cloudfront.net/2021/articles/2021-04-13-15-05/spooder.png/EG11/resize/450x-1/quality/75/format/jpg)
Capcom announced that restoring the internal systems affected by the attack is almost finished and that the investigation into the incident has completed. Investigators discovered that Ragnar Locker operators gained access to Capcom’s internal network by targeting an old VPN backup device located at the company’s North American subsidiary in California. From there, the attacker pivoted to devices in offices in the U.S. and Japan and detonated the file-encrypting malware on November 1st, causing email and file servers to be taken offline. Below is a simplified depiction of the incident.
Capcpm said that it was in the process of boosting network defenses when Ragnar Locker threat actor breached its network. The compromised VPN device was on its way out as new models had been installed.
However, on the background of the pandemic pushing for remote work, the old VPN server continued to function as an emergency backup in case of communication problems.
The company’s final assessment regarding the data breach is that 15,649 individuals have been impacted; that’s 766 less people than initially reported in January 2021.
The information did not include payment card details, only corporate and personal data that includes names, addresses, phone numbers, and email addresses. Capcom is currently notifying affected individuals.
Regarding the ransom, the game maker says that the threat actor left on encrypted systems a message that did not mention any price, just instructions to contact the attacker to engage in negotiations. Capcom says that following consultations with law enforcement, it did not engage Ragnar Locker ransomware operator and made no effort to contact them. This decision made the attacker leak company data a few weeks after the breach.
Part of Capcom's increased security measures since the cyber-attack are a security operations center (SOC) service that keeps an eye on external connections and an endpoint detection and response (EDR) system to check for unusual activity on PCs and servers.
![[Image: jpg]](https://d2skuhm0vrry40.cloudfront.net/2021/articles/2021-04-13-15-05/spooder.png/EG11/resize/450x-1/quality/75/format/jpg)
Capcom announced that restoring the internal systems affected by the attack is almost finished and that the investigation into the incident has completed. Investigators discovered that Ragnar Locker operators gained access to Capcom’s internal network by targeting an old VPN backup device located at the company’s North American subsidiary in California. From there, the attacker pivoted to devices in offices in the U.S. and Japan and detonated the file-encrypting malware on November 1st, causing email and file servers to be taken offline. Below is a simplified depiction of the incident.
Capcpm said that it was in the process of boosting network defenses when Ragnar Locker threat actor breached its network. The compromised VPN device was on its way out as new models had been installed.
However, on the background of the pandemic pushing for remote work, the old VPN server continued to function as an emergency backup in case of communication problems.
The company’s final assessment regarding the data breach is that 15,649 individuals have been impacted; that’s 766 less people than initially reported in January 2021.
The information did not include payment card details, only corporate and personal data that includes names, addresses, phone numbers, and email addresses. Capcom is currently notifying affected individuals.
Regarding the ransom, the game maker says that the threat actor left on encrypted systems a message that did not mention any price, just instructions to contact the attacker to engage in negotiations. Capcom says that following consultations with law enforcement, it did not engage Ragnar Locker ransomware operator and made no effort to contact them. This decision made the attacker leak company data a few weeks after the breach.
Part of Capcom's increased security measures since the cyber-attack are a security operations center (SOC) service that keeps an eye on external connections and an endpoint detection and response (EDR) system to check for unusual activity on PCs and servers.


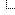
![[-] [-]](https://www.aiowares.com/images/collapse.png)


